Dod Zero Trust Awareness Course Answers
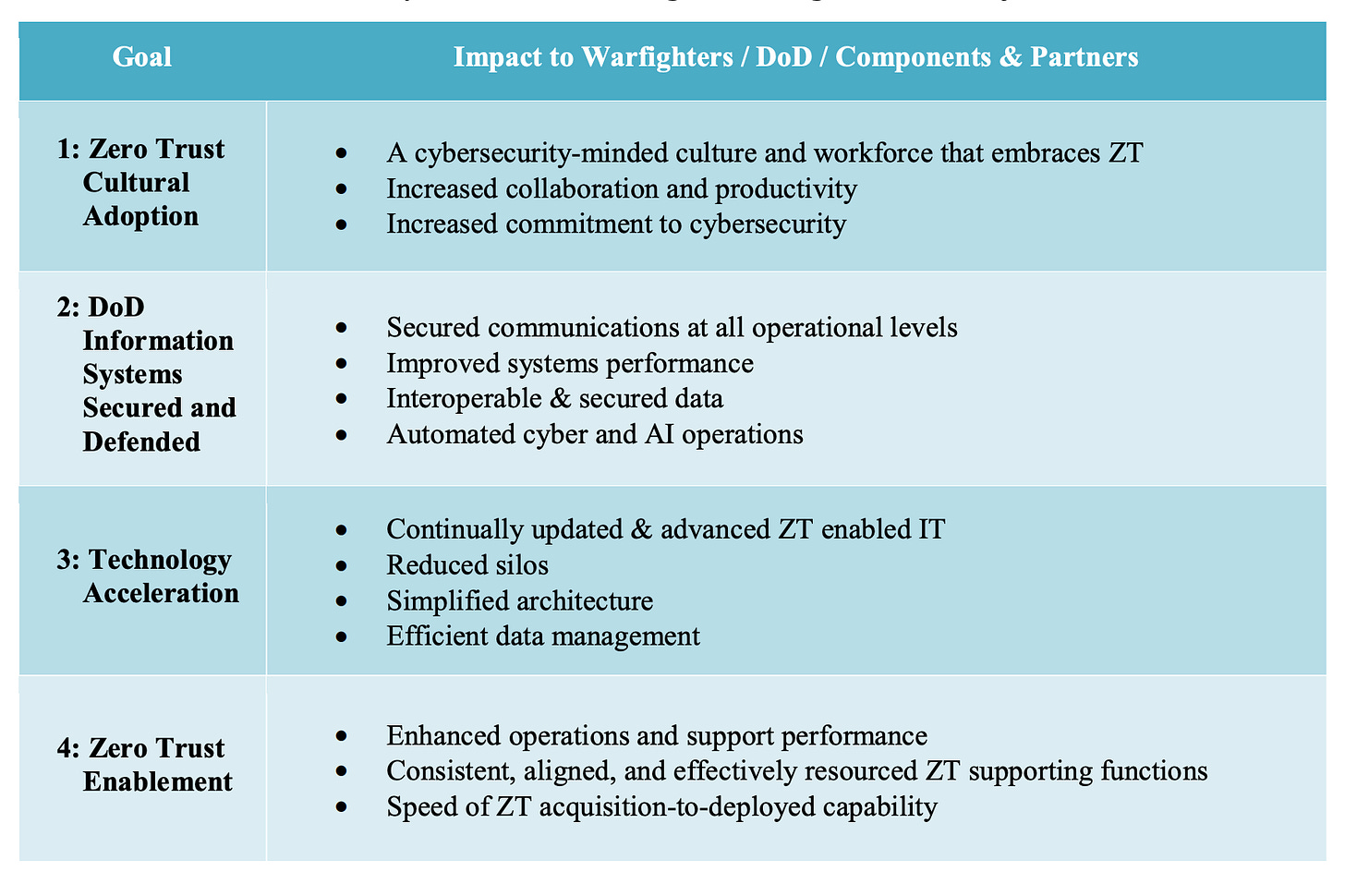
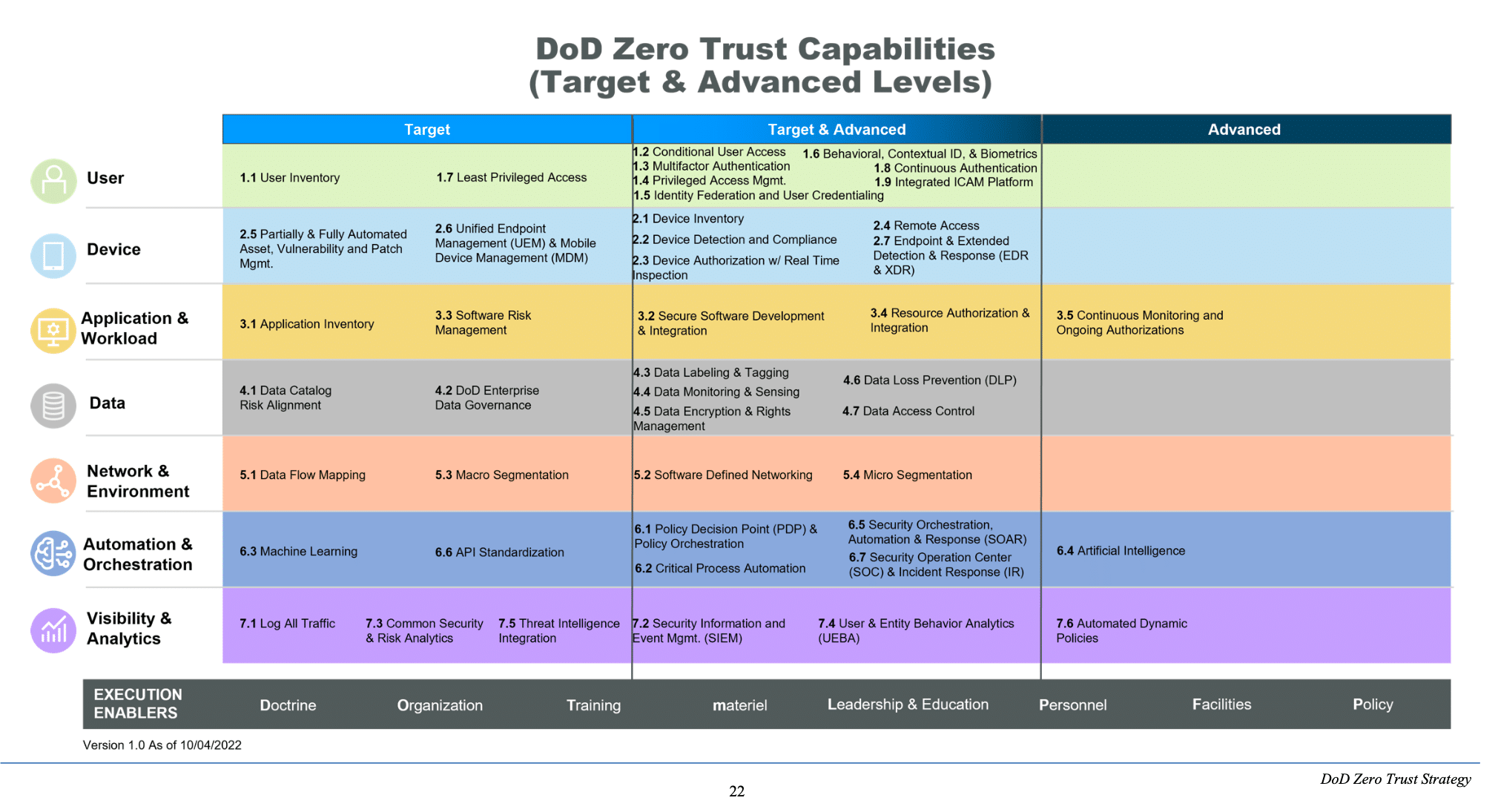
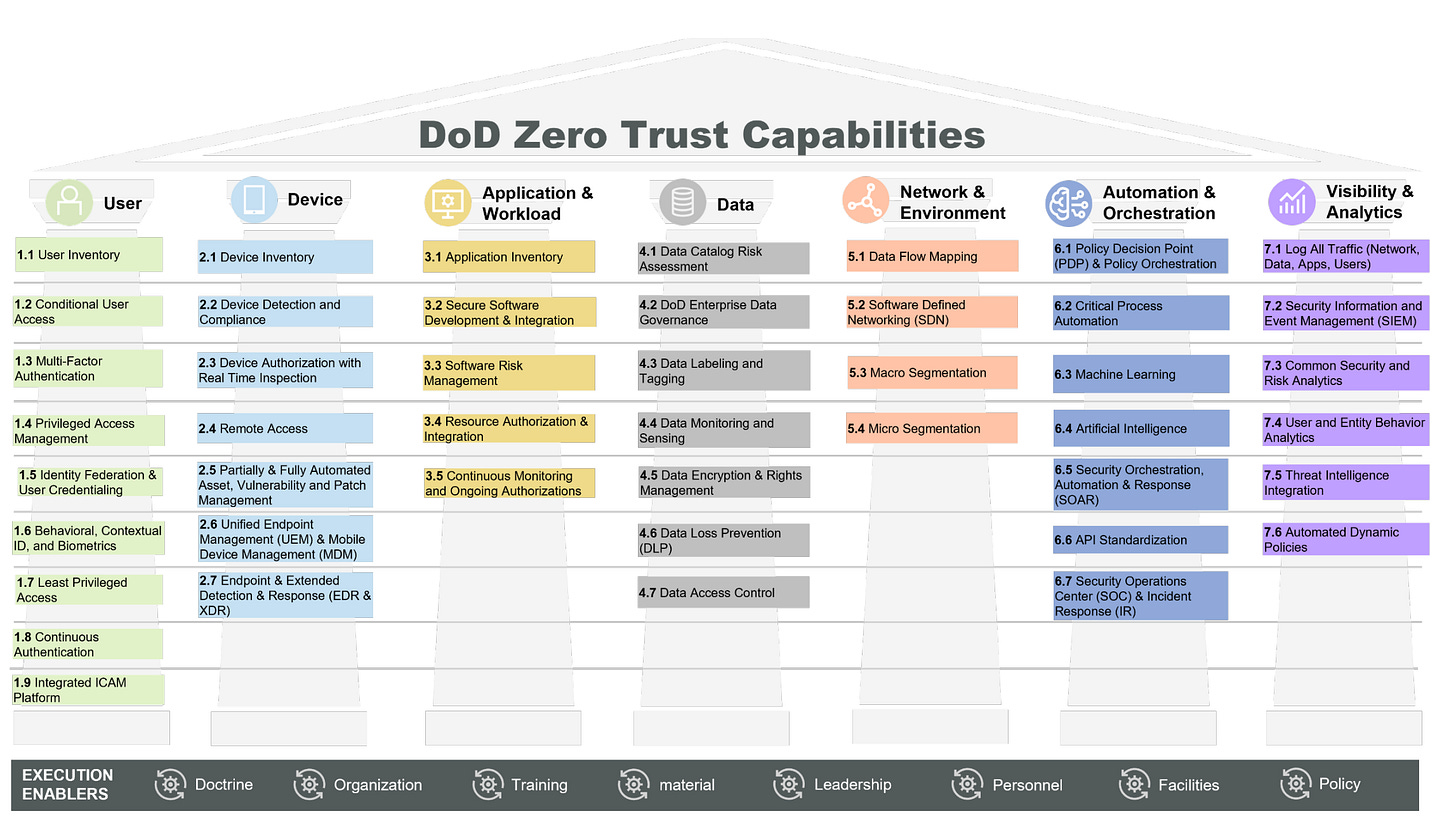
Dod Zero Trust Awareness Course Answers - Web the dod zero trust engineering team developed this zero trust reference architecture (zt ra) to align with the dod definition: How does fortinac dynamically control access to the network? Web dod zero trust target level is deemed to be the required minimum set of zero trust capability outcomes and activities necessary to secure and protect the department's data, applications, assets. 1) zt cultural adoption, 2) dod information systems secured and defended, 3) technology acceleration, 4) zt enablement. Web the zero trust awareness course is now available on jko as the department of defense (dod) rolls out its new zero trust strategy. Web here are the questions and answers : Detects a change in the device profile and automatically quarantines the device connects devices securely using ztna technology or vpn ssl authenticates devices using mfa before allowing access to the network Web based on dod zero trust strategy, the four (4) goals of zero trust are. Current and future cyber threats and attacks drive the need for a zero trust. Visit joint knowledge online, search for. The catalog covers topics such as joint doctrine, joint operations, joint planning, joint readiness, and joint professional development. 1) zt cultural adoption, 2) dod information systems secured and defended, 3) technology acceleration, 4) zt enablement. Web the dod zero trust engineering team developed this zero trust reference architecture (zt ra) to align with the dod definition: “reference architecture is an. Select the true statements concerning zero trust. Web monitor and maintain the network. It provides an awareness of the implications of implementing zero trust and explains why it is a critical concept that should become a. Web training & events resources other cybersecurity what is zero trust? What is the standard form of identification for dod employees? Current and future cyber threats and attacks drive the need for a zero trust. Visit joint knowledge online, search for. Web it provides an awareness of the implications of implementing zero trust and explains why it is a critical concept that should become a major focus for cybersecurity across the dod. 1) zt cultural adoption, 2) dod information systems secured. The first in a series of training courses designed to facilitate this movement begins with general awareness of zero trust for all audiences across the dod enterprise. Web the zero trust framework will reduce the attack surface, reduce risk, offer opportunities to manage the full range of risks (e.g., policy, programming, budgeting, execution,. Web the dod zero trust engineering team. (multiple choice) (o1) zt cultural adoption, 2) dod information systems secured and defended, 3) encryption, 4) cost reduction @ 1) zt cultural adoption, 2) dod information systems s. Select the true statements concerning zero trust. Study with quizlet and memorize flashcards containing terms like zero trust, traditional security vs. 1) zt cultural adoption, 2) dod information systems secured and defended,. Web certificate of competence in zero trust (cczt) outlines how to put specific measures in place to provide assurance that systems and their components operate appropriately and are continuously verified. Web training & events resources other cybersecurity what is zero trust? Web the zt pfmo began in january 2022. Web dod zero trust target level is deemed to be the. How does fortinac dynamically control access to the network? Web monitor and maintain the network. Web the zero trust framework will reduce the attack surface, reduce risk, offer opportunities to manage the full range of risks (e.g., policy, programming, budgeting, execution,. Web the dod zero trust engineering team developed this zero trust reference architecture (zt ra) to align with the. Visit joint knowledge online, search for. Randy resnick, the director of the zero trust portfolio management office at dod, said training, education and listening are huge factors in ensuring this program’s success. Detects a change in the device profile and automatically quarantines the device connects devices securely using ztna technology or vpn ssl authenticates devices using mfa before allowing access. Study with quizlet and memorize flashcards containing terms like zero trust, traditional security vs. Web the dod zero trust engineering team developed this zero trust reference architecture (zt ra) to align with the dod definition: What is the standard form of identification for dod employees? Web (multiple choice) o devices o applications & workloads o network & environment @ data. Visit joint knowledge online, search for. Web here are the questions and answers : “reference architecture is an authoritative source of information about a specific subject area that guides and constrains the instantiations of multiple architectures and solutions.” 3 Today, the department of defense released the department of defense zero trust strategy and roadmap. The catalog covers topics such as. Web study with quizlet and memorize flashcards containing terms like zero trust, benefits of zero trust network, core zero trust principles and more. Today, the department of defense released the department of defense zero trust strategy and roadmap. “reference architecture is an authoritative source of information about a specific subject area that guides and constrains the instantiations of multiple architectures and solutions.” 3 Web study with quizlet and memorize flashcards containing terms like zero trust, password, multifactor authentication (mfa) and more. Web here are the questions and answers : Web certificate of competence in zero trust (cczt) outlines how to put specific measures in place to provide assurance that systems and their components operate appropriately and are continuously verified. Randy resnick, the director of the zero trust portfolio management office at dod, said training, education and listening are huge factors in ensuring this program’s success. How does fortinac dynamically control access to the network? The catalog covers topics such as joint doctrine, joint operations, joint planning, joint readiness, and joint professional development. Study with quizlet and memorize flashcards containing terms like zero trust, traditional security vs. Web monitor and maintain the network. The first in a series of training courses designed to facilitate this movement begins with general awareness of zero trust for all audiences across the dod enterprise. Tim denman, dau cyber learning director, began a rotational assignment in march with the goal of developing three levels of zero trust training. (multiple choice) (o1) zt cultural adoption, 2) dod information systems secured and defended, 3) encryption, 4) cost reduction @ 1) zt cultural adoption, 2) dod information systems s. Visit joint knowledge online, search for. Web the dod zero trust engineering team developed this zero trust reference architecture (zt ra) to align with the dod definition: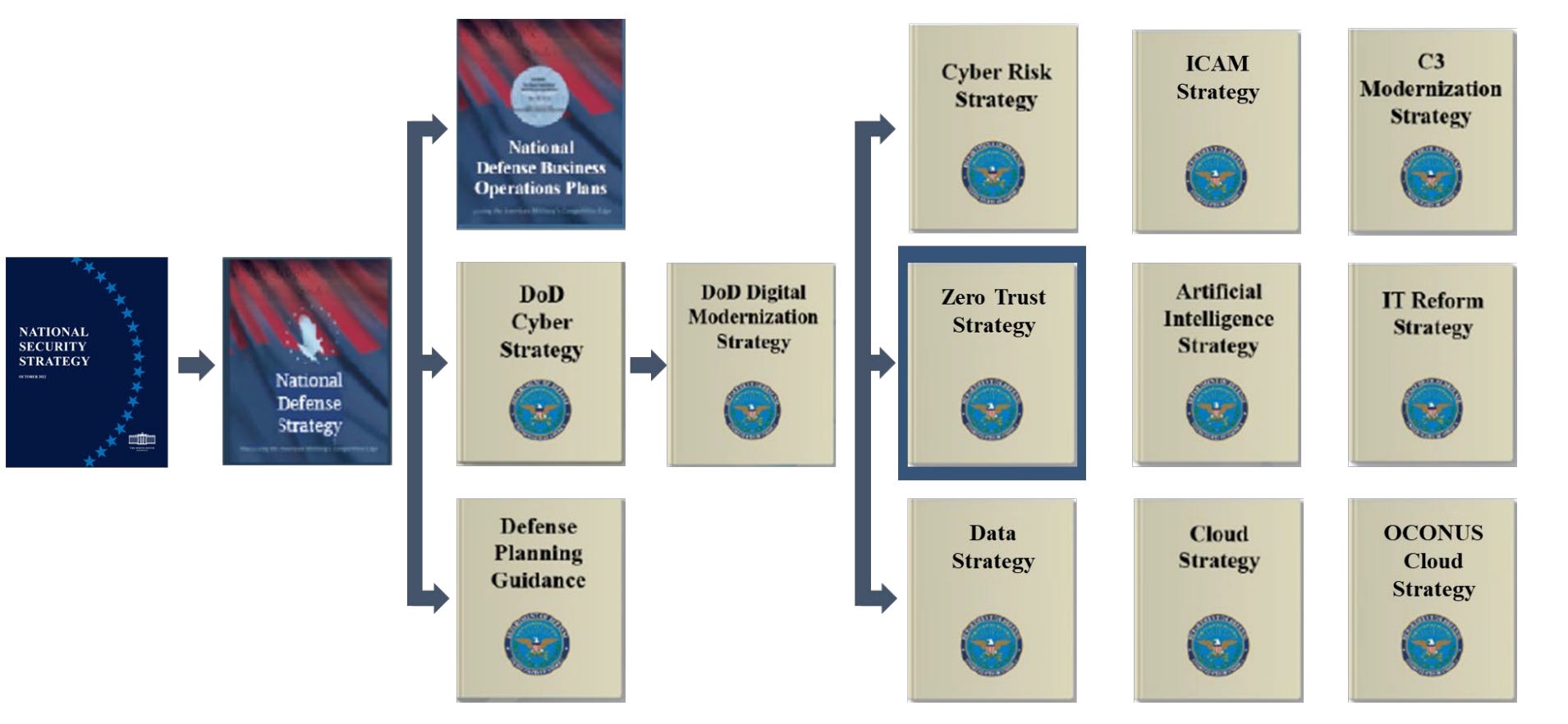
A look at the DoD's Zero Trust Strategy by Chris Hughes

What is the Department of Defense Zero Trust strategy 2022, and how to
A look at the DoD's Zero Trust Strategy by Chris Hughes
How The US Defense Department Can Evolve and Execute Their Zero Trust
A look at the DoD's Zero Trust Strategy by Chris Hughes

Zero Trust and Identity Management A Game Changer for DoD Network Security
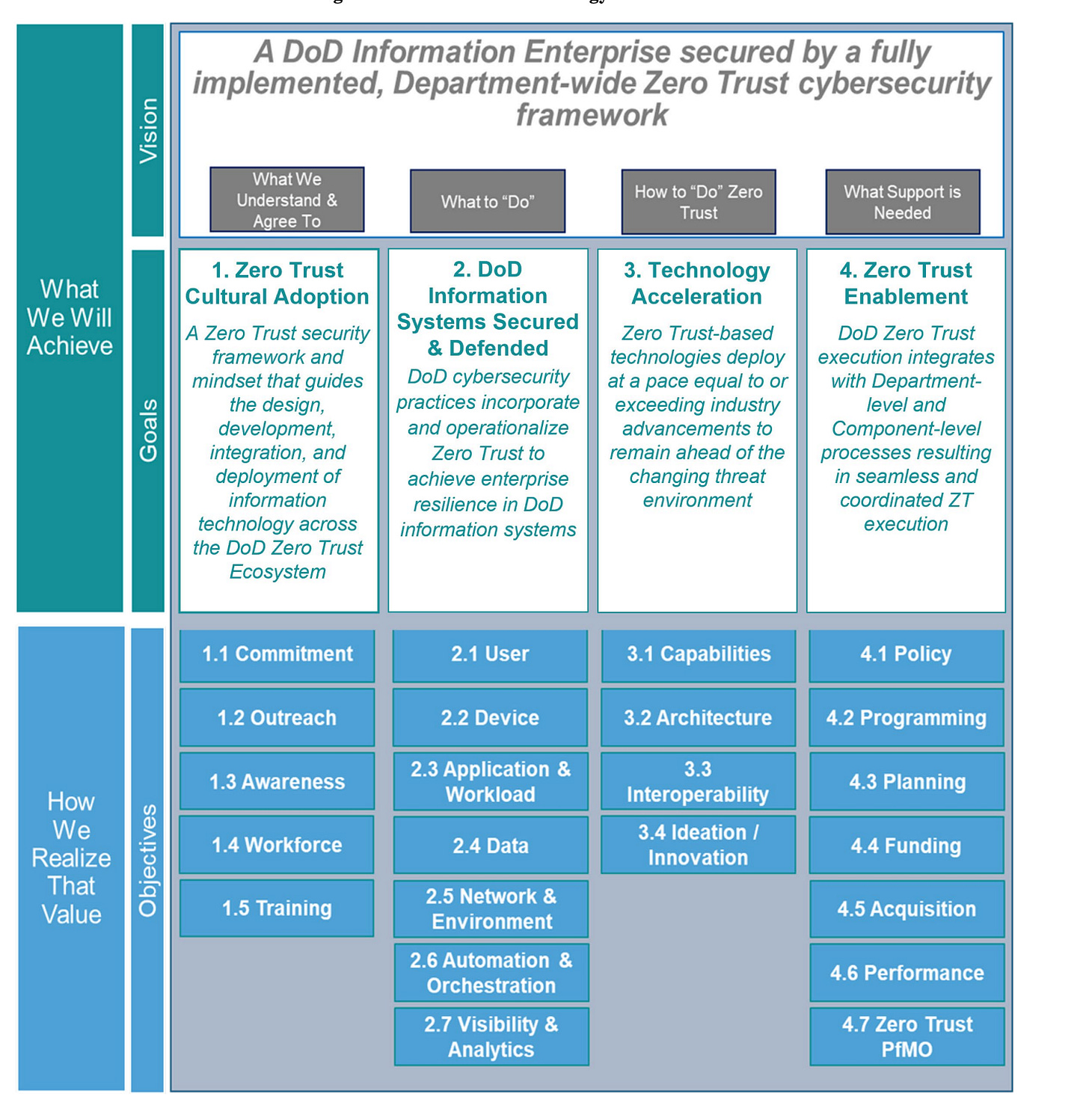
A look at the DoD's Zero Trust Strategy by Chris Hughes
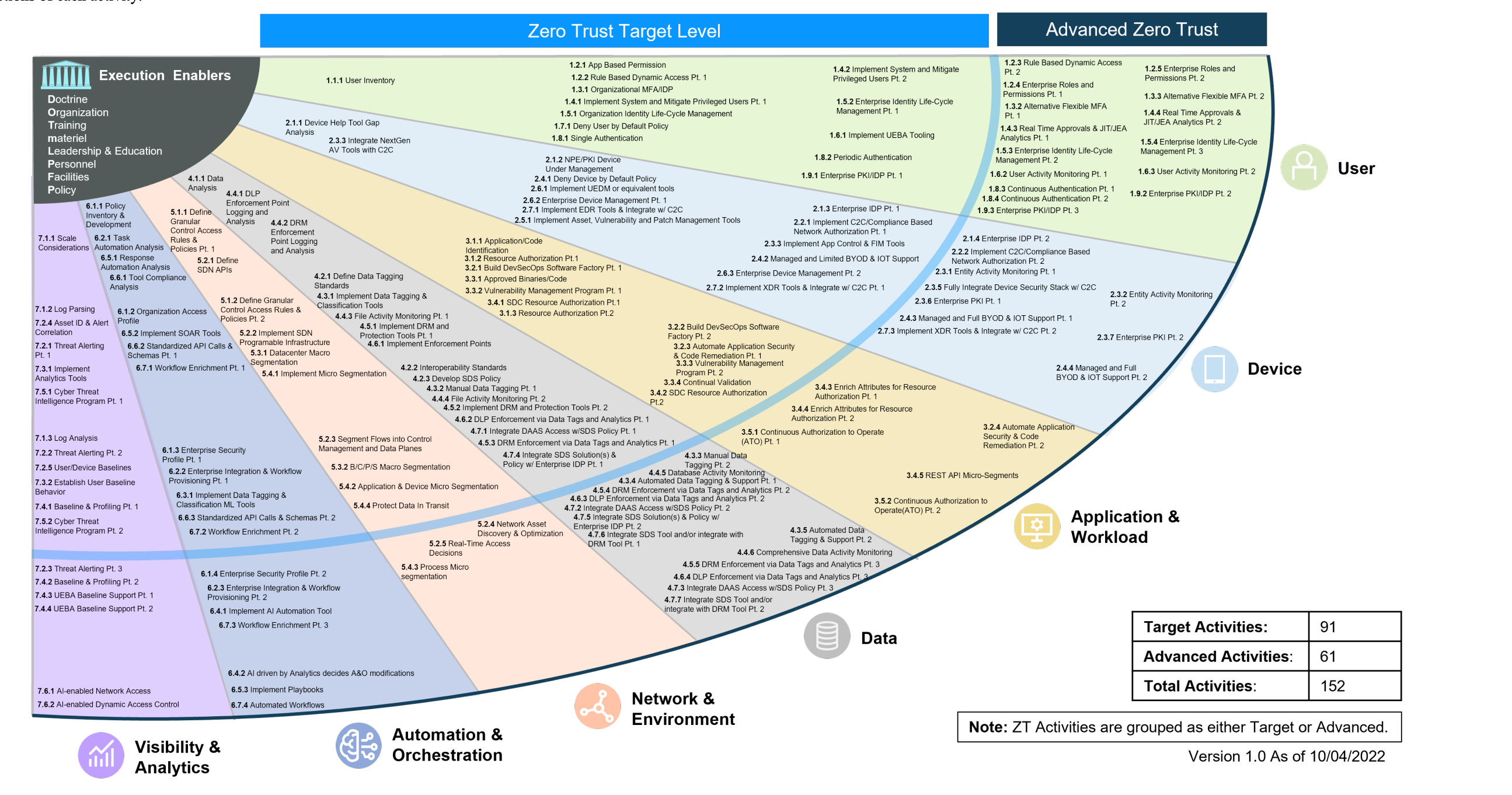
A look at the DoD's Zero Trust Strategy by Chris Hughes

A look at the DoD's Zero Trust Strategy by Chris Hughes
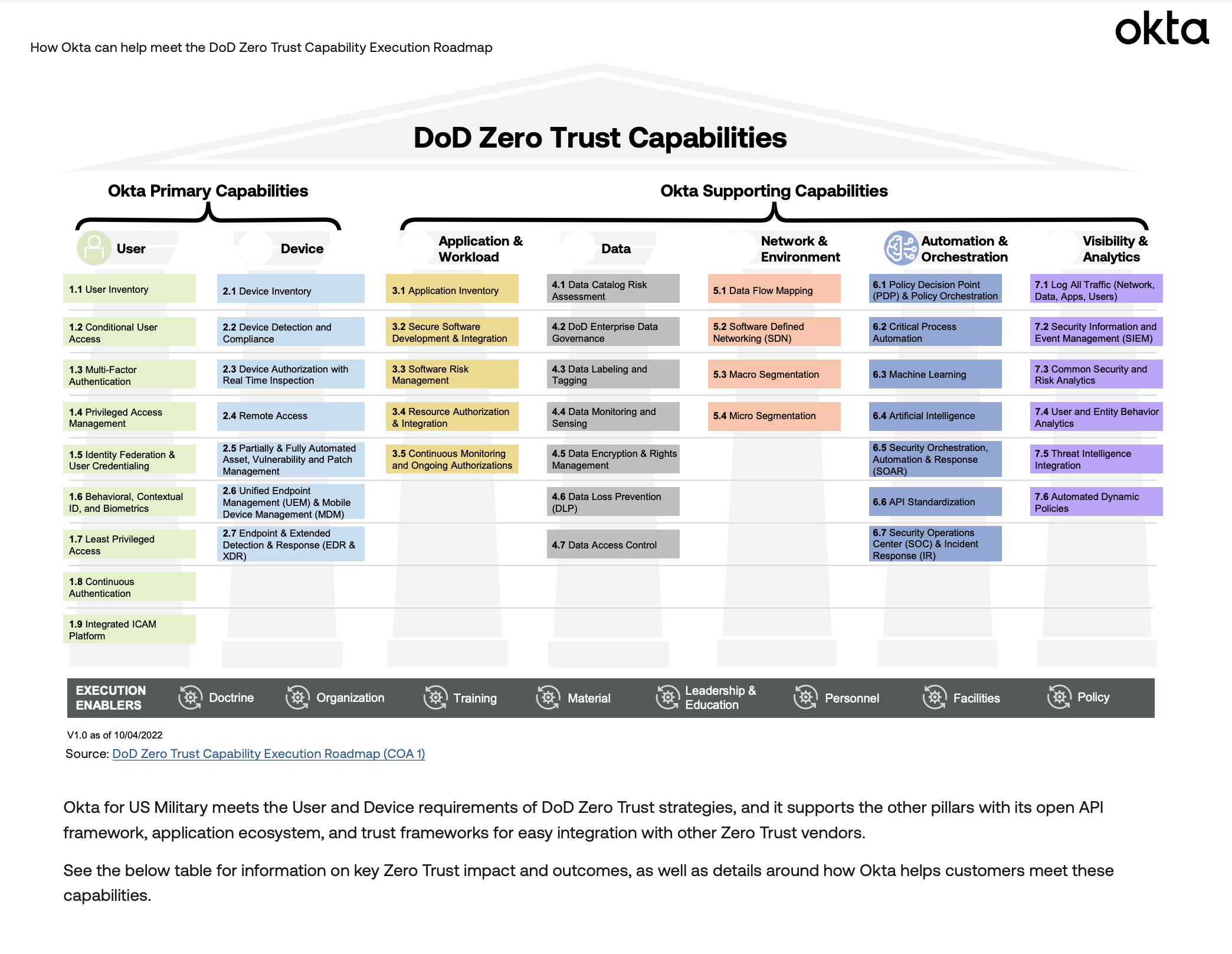
How Okta can help meet the DoD Zero Trust Capability Execution Roadmap
Current And Future Cyber Threats And Attacks Drive The Need For A Zero Trust.
Web The Road Show Is Just One Way The Portfolio Management Office Is Leading The Effort To Meet The Pentagon’s 2027 Deadline To Implement Zero Trust.
The Awareness Course Is Now Available On Jko And An Executive Level Online Course That Is Expected To Follow In February Will Make Up The Level 1 Training.
Web Training & Events Resources Other Cybersecurity What Is Zero Trust?
Related Post: